50 Shocking Mind-Boggling Cyber Security Statistics Facts for 2024

Here are 10 shocking cyber security statistics for 2024:
- 1. Cybercrime is projected to cause damages worth $10.5 trillion globally by 2024.
- 2. A new ransomware attack occurs every 11 seconds.
- 3. By 2024, it is estimated that there will be 300 billion passwords in use worldwide.
- 4. Phishing attacks account for 90% of all data breaches.
- 5. The average cost of a data breach is expected to exceed $150 million by 2024.
- 6. Cybersecurity spending is predicted to reach $248 billion by 2024.
- 7. Small businesses are the target of 43% of all cyberattacks.
- 8. By 2024, there will be a shortage of 3.5 million cybersecurity professionals.
- 9. Mobile malware attacks are expected to increase by 50% in 2024.
- 10. Artificial intelligence (AI) will be used in 95% of cybersecurity solutions by 2024.
The Growing Threat of Cybercrime
Cybercrime is a rapidly growing threat in today's digital world.
With the increasing reliance on technology and interconnectedness, individuals and organizations are becoming more vulnerable to cyber attacks.
Here are some mind-boggling statistics that highlight the severity of the situation:
The Global Cost of Cybercrime

1. Cybercrime is projected to cause damages worth $10.5 trillion globally by 2024.
This staggering figure includes the costs associated with data breaches, ransomware attacks, and other cyber threats.
It highlights the immense financial impact that cybercrime can have on individuals, businesses, and economies as a whole.
The Frequency of Ransomware Attacks

2. A new ransomware attack occurs every 11 seconds.
Ransomware is a type of malware that encrypts a victim's files and demands a ransom in exchange for their release.
These attacks can be devastating for individuals and organizations, often resulting in significant financial losses and reputational damage.
The Proliferation of Passwords

3. By 2024, it is estimated that there will be 300 billion passwords in use worldwide.
Passwords are a common method of authentication, but they are also a weak point in cybersecurity.
With the increasing number of online accounts and services, individuals often struggle to create and remember strong, unique passwords for each platform they use.
This creates opportunities for cybercriminals to exploit weak passwords and gain unauthorized access to sensitive information.
The Dominance of Phishing Attacks

4. Phishing attacks account for 90% of all data breaches.
Phishing is a technique used by cybercriminals to trick individuals into revealing sensitive information, such as login credentials or financial details.
These attacks often involve deceptive emails, websites, or messages that appear legitimate but are designed to steal personal information.
The prevalence of phishing attacks highlights the importance of user awareness and education in preventing cybercrime.
The Cost of Data Breaches

5. The average cost of a data breach is expected to exceed $150 million by 2024.
Data breaches can have severe financial and reputational consequences for organizations.
They often result in the loss or theft of sensitive customer information, leading to legal liabilities, regulatory fines, and damage to brand reputation.
Investing in robust cybersecurity measures is crucial for mitigating the risks associated with data breaches.
The Importance of Cybersecurity Investment
Given the growing threat of cybercrime, organizations are increasingly recognizing the need to invest in cybersecurity measures.
Here are some statistics that highlight the scale of cybersecurity spending:
The Rising Cost of Cybersecurity

6. Cybersecurity spending is predicted to reach $248 billion by 2024.
This significant investment reflects the increasing importance placed on protecting digital assets and sensitive information.
Organizations are allocating more resources to cybersecurity to defend against evolving threats and stay ahead of cybercriminals.
The Vulnerability of Small Businesses

7. Small businesses are the target of 43% of all cyberattacks.
Despite their size, small businesses often lack the resources and expertise to implement robust cybersecurity measures.
This makes them attractive targets for cybercriminals who see them as easier entry points into larger networks or sources of valuable data.
It is crucial for small businesses to prioritize cybersecurity and adopt proactive measures to protect their assets.
The Shortage of Cybersecurity Professionals

8. By 2024, there will be a shortage of 3.5 million cybersecurity professionals.
The demand for skilled cybersecurity experts is rapidly outpacing the supply.
This shortage poses a significant challenge for organizations seeking to strengthen their cybersecurity defenses.
It also highlights the need for educational institutions and governments to invest in cybersecurity training and initiatives to bridge this skills gap.
The Rise of Mobile Malware
9. Mobile malware attacks are expected to increase by 50% in 2024.
As smartphones and mobile devices become integral parts of our daily lives, they also become attractive targets for cybercriminals.
Mobile malware can compromise personal data, intercept communications, and even gain control over a device.
With the increasing reliance on mobile technology, it is crucial to implement robust security measures to protect against mobile threats.
The Role of Artificial Intelligence in Cybersecurity
10. Artificial intelligence (AI) will be used in 95% of cybersecurity solutions by 2024.
AI has the potential to revolutionize cybersecurity by automating threat detection, response, and prevention.
Machine learning algorithms can analyze vast amounts of data to identify patterns and anomalies that may indicate a cyber attack.
Integrating AI into cybersecurity strategies can enhance the efficiency and effectiveness of defense mechanisms.
Conclusion
The statistics presented here paint a sobering picture of the current state of cyber security.
The growing threat of cybercrime, the rising costs of data breaches, and the shortage of skilled professionals all highlight the need for organizations and individuals to prioritize cybersecurity.
Investing in robust security measures, staying informed about emerging threats, and adopting best practices can help mitigate the risks associated with cyber attacks.
As technology continues to advance, it is crucial to remain vigilant and proactive in protecting our digital assets and personal information.
Want To Get More Traffic To Your Site?
Over 15,763 SEO agencies and brands are using AtOnce to rank higher on Google.
It lets you write hundreds of articles on any topic, giving you more clicks to your site.
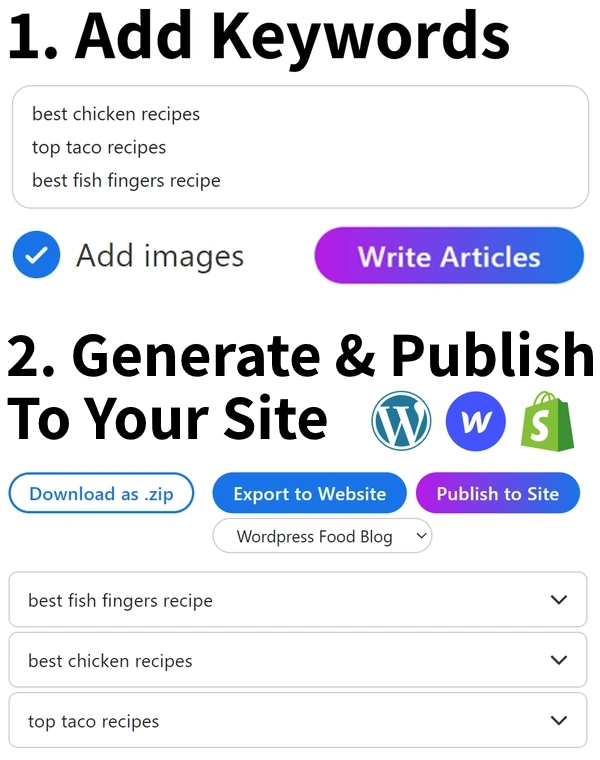
Get more traffic and sales — without wasting months of your time.
Click Here To Learn More
What are some mind boggling cyber security statistics facts?
What are the latest cyber security statistics facts?
Can you share some interesting cyber security statistics facts?

Asim is the CEO & founder of AtOnce. After 5 years of marketing & customer service experience, he's now using Artificial Intelligence to save people time.
Read This Next
50 Ultimate Steps: Mastering Comprehensive Background Investigations 202450 Shocking Facts: Super Bowl Attendance Numbers Unveiled - 202450 Top-Rated Platforms for Complimentary F1 Streaming 202450 Shocking Hulu Statistics: 2024's Ultimate Guide










