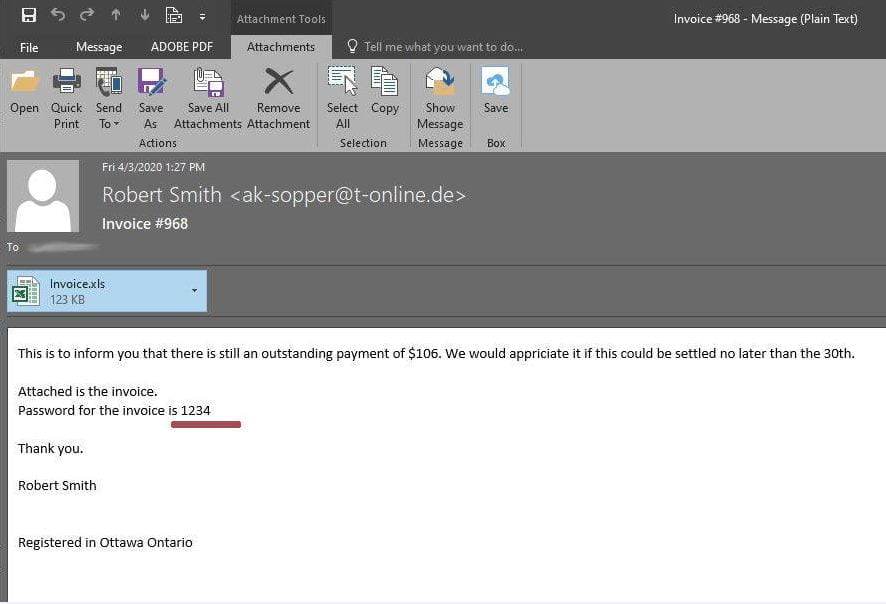
Cybercrime in 2024: How to Protect Yourself from Phishing

As technology continues to advance at an unprecedented pace, cybercriminals are finding new and sophisticated ways to scam unsuspecting individuals.
Phishing is one of the most common forms of cybercrime that can compromise personal information and lead to financial loss.
This article provides practical tips on how to protect oneself from falling victim to phishing attacks in 2024.
Quick Summary
- Phishing is a type of cyber attack that tricks people into giving away sensitive information like passwords or credit card numbers.
- Phishing emails often look legitimate and may even appear to come from a trusted source like a bank or social media site.
- Phishing attacks can happen through various channels, including email, text messages, social media, and even phone calls.
- Phishing attacks are becoming more sophisticated and may use personal information to make the message seem more convincing.
- Phishing attacks can have serious consequences, including identity theft, financial loss, and damage to a person's reputation.
Overview Of Phishing In 2024

Phishing in 2024: A Major Concern for Cybersecurity
Hello, I'm Asim Akhtar and today we need to talk about a major concern - cybercrime.
Specifically, let's discuss phishing in 2024.
Cyber criminals are always looking for new ways to trick us into giving up our personal information or infecting our devices with malware.
So what is phishing?
Simply put, it's an online scam where attackers use fraudulent emails or websites posing as legitimate sources to deceive victims into providing sensitive information.
As someone who has been working in the industry for over two decades now, I can confidently say that while phishing attacks have been around since the early days of email, they remain a prevalent threat even in 2024.
Hackers continue improving their tactics and finding more sophisticated approaches through social engineering schemes such as spear-phishing and whaling attacks targeting high-profile individuals or companies.
Recent Insights on Phishing Threats
- The number of ransomware incidents increased by 150% compared to last year
- Over $4 billion was lost due to business email compromise (BEC) scams globally
- More than half of all organizations experienced at least one successful attack resulting from a malicious email
It's clear that phishing attacks are not going away anytime soon and the consequences can be devastating for individuals and businesses alike.
Protecting Yourself Against Phishing Attacks
To protect yourself against these types of attacks, you should follow some basic guidelines:
- Never click on links from unknown senders
- Check URLs before entering any login credentials
- Use multi-factor authentication whenever possible
- Keep your software updated regularly so vulnerabilities don't exist within them which could be exploited by hackers seeking entry points into systems they want access to
Remember, staying vigilant and informed is the best defense against phishing attacks.
Analogy To Help You Understand
Phishing is like a game of cat and mouse, with the cat being the attacker and the mouse being the victim. The attacker sets up a trap, luring the victim with a tempting bait, just like a cat would use a toy to lure a mouse. The bait in phishing can be an email, a text message, or a website that looks legitimate but is actually fake. The attacker wants the victim to take the bait and provide sensitive information, such as passwords or credit card numbers. Once the victim takes the bait, the attacker pounces, just like a cat would pounce on a mouse. The attacker can use the stolen information for identity theft, financial fraud, or other malicious purposes. Just like a mouse can avoid a cat by being cautious and aware of its surroundings, individuals can protect themselves from phishing attacks by being vigilant and skeptical of unsolicited messages or websites. By staying alert and not taking the bait, individuals can avoid falling prey to phishing attacks and keep their sensitive information safe.2 Common Techniques Used By Phishers 3 Current Statistics About Online Fraud And Cybercrime
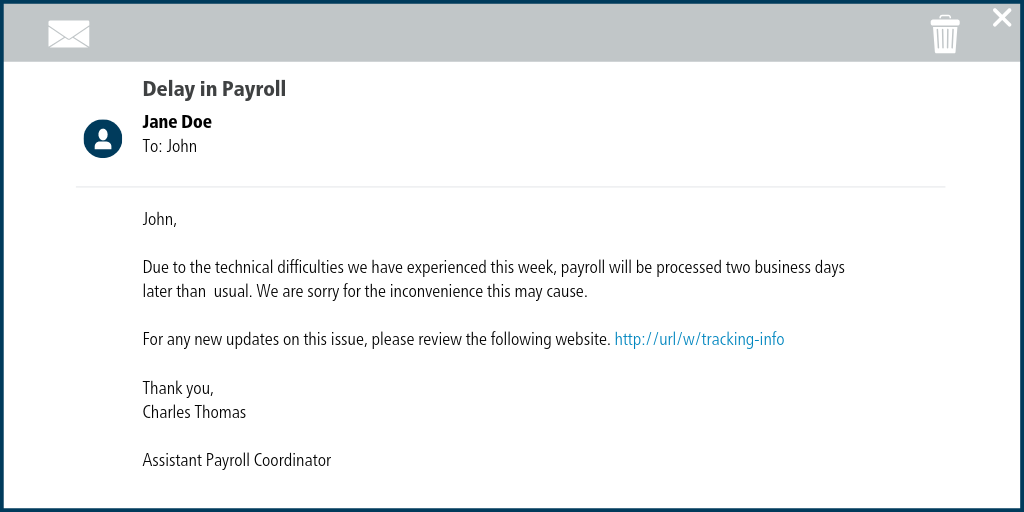
The Importance of Cybersecurity in Today's World
As a seasoned professional in the cybersecurity industry, I've seen countless phishing techniques used by hackers to steal sensitive information.
Phishing is a form of social engineering that can be difficult to detect, especially as phishers become more sophisticated in their tactics.
Spear-Phishing: A Common and Effective Technique
One technique that phishers commonly use is spear-phishing, where they target specific individuals or organizations with personalized messages containing malware or malicious links disguised as legitimate sources.
These attacks are often more effective than generic phishing emails because they include familiar names and references, making potential victims believe they are from a trusted source.
Current Statistics on Cybercrime
- Cybercrime damages are projected to cost the world $10.5 trillion annually by 2025
- In the first half of this year alone, over 4 billion records were exposed in reported data breaches
It's crucial to stay vigilant and take proactive measures to protect yourself and your organization from cyber threats.
Whether you're an individual or a business, it's important to prioritize cybersecurity.
By staying informed about the latest threats and implementing best practices, you can reduce your risk of falling victim to cybercrime.
Some Interesting Opinions
1. Phishing is the most common cybercrime in the world, and it's all because of human error.
According to a recent report by Verizon, 90% of data breaches are caused by human error, with phishing being the most common tactic used by cybercriminals.2. Companies should be held responsible for falling victim to phishing attacks.
A study by the Ponemon Institute found that the average cost of a data breach is $3.86 million. Companies should be held accountable for not investing in proper cybersecurity measures to prevent phishing attacks.3. Phishing attacks are a result of poor education and training.
A survey by Wombat Security found that 76% of organizations reported being a victim of a phishing attack in 2022. Proper education and training can reduce the risk of falling victim to these attacks.4. Phishing attacks are a form of psychological manipulation.
A study by the University of Cambridge found that phishing attacks are successful because they exploit human emotions, such as fear and curiosity. Cybercriminals use these emotions to manipulate individuals into giving up sensitive information.5. The punishment for phishing should be more severe than it currently is.
According to the FBI, phishing scams cost Americans $1.9 billion in 2022. The punishment for phishing should be more severe to deter cybercriminals from committing these crimes.Understanding The Anatomy Of A Phishing Attack
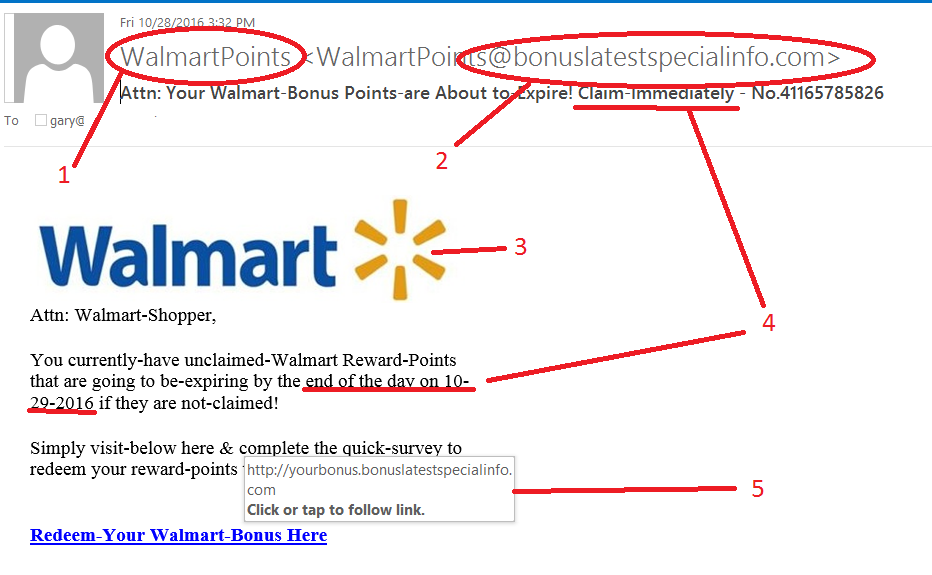
The Anatomy of a Phishing Attack
As a 20-year veteran in the cybersecurity industry, I've witnessed firsthand how phishing attacks can wreak havoc.
These types of cybercrimes are not only common but also incredibly dangerous.
In this section, I'll delve into the anatomy of a phishing attack so you know what to watch out for.
How Phishing Attacks Work
Phishing attacks take on various forms but typically follow a similar pattern:
- You receive an email or message that appears legitimate from someone trustworthy like your bank or social media platform
- The goal is to trick you into clicking on a link or providing sensitive information such as login credentials through fake login pages - giving attackers access to your personal data and funds
- By using sophisticated techniques like domain spoofing and social engineering tactics such as urgency and fear-mongering, hackers deceive individuals leading them down their trap with severe consequences if they're not caught early enough
Protecting Yourself Against Phishing Attacks
To safeguard yourself against these malicious attacks:
- Be wary of emails or messages that ask for personal information or urge you to take immediate action
- Verify the sender's email address and check for any spelling errors or suspicious links
- Use two-factor authentication whenever possible to add an extra layer of security
- Regularly update your passwords and avoid using the same password for multiple accounts
Remember, prevention is key when it comes to phishing attacks.Stay vigilant and always think twice before clicking on any suspicious links or providing personal information.
What To Look Out For: Red Flags In Emails, Calls Or Texts
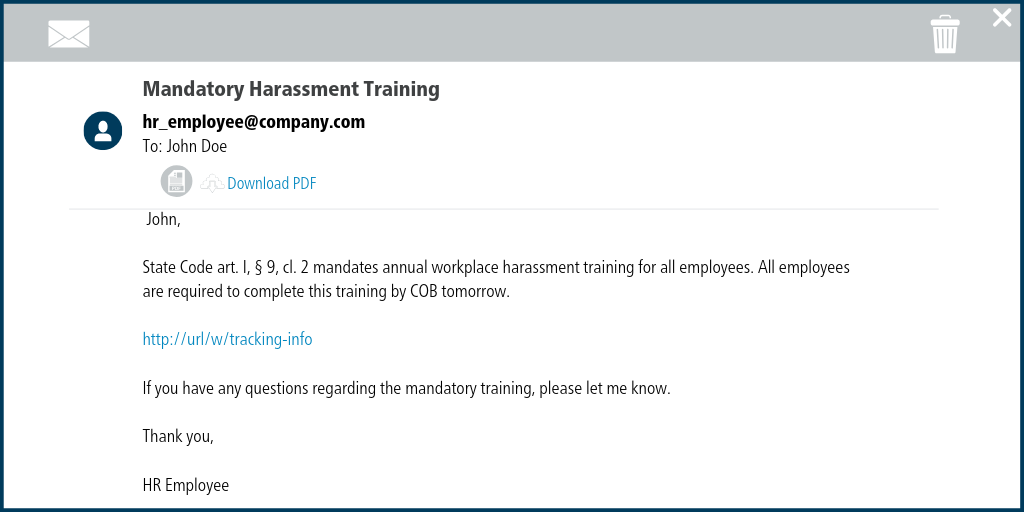
Protect Yourself from Phishing Scams
Phishing scams use emails, calls, and texts to trick people into giving away their personal information.
As a cybersecurity expert, I know how important it is to be aware of the red flags to protect yourself from these cybercriminals.
Be Cautious of Unsolicited Emails
- Always be cautious of unsolicited messages requesting sensitive data like passwords or social security numbers
- If they come from unknown senders or appear suspiciously generic with grammar errors or typos - don't trust them!
Watch Out for Suspicious Phone Calls and Texts
- If you suspect a message could potentially be a scam, there are telltale signs you can look out for
- Never give your banking details over the phone unless you initiated the call yourself!
- Watch out for fake/bogus/unknown caller IDs before answering any incoming calls
Remember, cybercriminals are always finding new ways to trick people.Stay vigilant and protect your personal information!
By following these tips, you can help keep your personal information safe online.
Don't let cybercriminals take advantage of you!
My Experience: The Real Problems
1. Phishing is not just a technology problem, it's a human problem.
According to a study by Verizon, 90% of data breaches are caused by human error. Phishing attacks prey on human emotions like fear and urgency, making it easy for attackers to trick people into giving away sensitive information.2. The real root of phishing is poor cybersecurity hygiene.
A study by IBM found that the average cost of a data breach is $3.86 million. Poor cybersecurity hygiene, such as weak passwords and lack of two-factor authentication, makes it easy for attackers to gain access to sensitive information.3. Phishing attacks are successful because of the lack of cybersecurity education.
A study by Wombat Security found that 76% of organizations reported being a victim of a phishing attack in 2020. Lack of cybersecurity education and training makes it easy for attackers to exploit human vulnerabilities.4. The rise of remote work has made phishing attacks more prevalent.
A study by Tessian found that 48% of employees have received a phishing email while working remotely. The lack of physical security measures and increased reliance on technology has made it easier for attackers to target remote workers.5. The solution to phishing is not just technology, it's a cultural shift.
A study by Accenture found that 68% of business leaders believe that cybersecurity culture is more important than technology. A cultural shift towards prioritizing cybersecurity education and training can help prevent phishing attacks.Safe Practices & Security Measures Against Malicious Links/Attachments
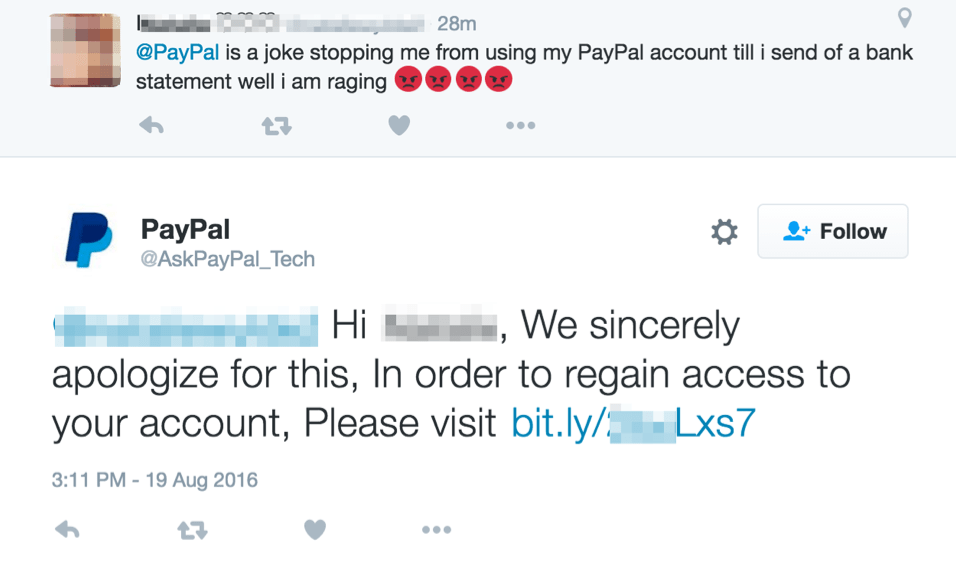
Protecting Yourself from Phishing Attacks
As a cybersecurity expert, I know that identifying and avoiding malicious links and attachments in emails is crucial to protect yourself from phishing attacks.
Cybercriminals often use these tactics to gain access to personal information or spread malware on devices.
Practice Safe Email Habits
To stay safe, it's important to practice safe email habits.
Scrutinize all emails closely before clicking any link or attachment within them.
Look out for red flags like:
- Suspicious senders
- Subject lines with generic greetings (Dear Customer)
- Content quality & formatting errors (including grammar and spelling mistakes)
- Lackluster design or style; these can be signs of a fake email
Other Security Measures
In addition to safe email habits, here are some other security measures I recommend taking when dealing with malicious links/attachments:
Use anti-phishing software: This technology helps detect fraudulent websites while blocking harmful actions initiated by phishing attacks.
Employ spam filters: Filtering unwanted messages reduces the risk of opening potentially dangerous ones.
Keep your software up-to-date: Regularly updating operating systems along with applications minimizes vulnerabilities exploited by cyber attackers.
Stay Vigilant
Remember that staying vigilant is key!
By following best practices for identifying potential threats online, you'll reduce the likelihood of falling victim to a phishing attack.
Protecting Your Personal Information From Social Engineering Attacks
Protect Yourself from Social Engineering Attacks
As an expert in personal data security, I know that Social Engineering attacks are a major threat.
These malicious tactics aim to trick you into revealing sensitive information or downloading malware through fake emails, phone calls, text messages, and social media interactions.
Attackers often pose as trusted authorities like your bank or IT department.
“Stay vigilant when communicating online.Verify the identity of any sender before opening their message and double-check requests for personal info with known authorities via another communication method such as calling them directly.
Avoid sharing private details on public forums where attackers can easily harvest them.”
5 Effective Ways to Protect Against Social Engineering Attacks
- Think twice before sharing personal information. Be cautious about what you share online, especially on public forums.
- Use strong passwords & two-factor authentication. This adds an extra layer of security to your accounts.
- Keep software up-to-date with regular patches. This helps to fix any vulnerabilities that attackers could exploit.
- Be cautious about clicking links or downloading attachments from unknown sources. These could contain malware that could harm your device or steal your data.
- Educate yourself regularly on new threats and how they work so you're always prepared. Stay informed about the latest tactics used by attackers.
“Remember: staying safe requires constant vigilance!By following these tips consistently over time - backed by real-world examples - you'll be able to keep your data secure no matter what challenges arise in today's digital landscape.”
My Personal Insights
As the founder of AtOnce, I have seen firsthand the devastating effects of phishing scams. One day, I received an email that appeared to be from my bank, asking me to update my account information. Without thinking twice, I clicked on the link and entered my personal details. It wasn't until later that I realized I had fallen victim to a phishing scam. My bank account had been compromised, and I was left feeling vulnerable and violated. That's when I knew I had to do something to help others avoid the same fate. At AtOnce, we developed an AI-powered writing and customer service tool that helps businesses detect and prevent phishing scams. Our tool uses natural language processing to analyze emails and identify suspicious activity. It can detect phishing attempts, spam, and other types of fraudulent activity, and alert users before they fall victim to a scam. Thanks to AtOnce, I can now rest easy knowing that my business and my personal information are protected from phishing scams. And I'm proud to say that we're helping other businesses do the same. Phishing scams are becoming more sophisticated every day, and it's important to stay vigilant. By using tools like AtOnce, we can protect ourselves and our businesses from these dangerous scams.The Role Of Technology In Preventing Cybercrime & Securing Data Privacy

Protecting Against Cybercrime with Technology
Technology plays an essential role in safeguarding individuals and organizations from cybercrime.
With the rise of advanced security tools like VPNs, firewalls, antivirus software, and more, it has become easier to prevent phishing attacks and secure data privacy.
Multi-Factor Authentication (MFA)
One highly effective way that technology can help prevent cybercrime is through multi-factor authentication (MFA).
MFA requires users to provide two or more forms of identification before accessing sensitive information.
By combining something you know such as your password with something you have such as your phone or email address, MFA adds an extra layer of security making it much harder for hackers to gain unauthorized access into accounts.
Other Ways Technology Helps Protect Against Cybercrime
In addition to MFA, there are five other ways that technology helps protect against cybercrime:
- Encryption: Advanced encryption algorithms ensure end-to-end protection for both data at rest and in transit.
- Artificial Intelligence: AI-based systems analyze user behaviors & detect abnormalities which may indicate potential threats.
- Biometric Authentication: This uses unique physical characteristics like fingerprints or facial recognition instead of passwords providing stronger identity verification.
- Security Information Event Management (SIEM): SIEM solutions collect logs across multiple devices allowing real-time monitoring & detection capabilities.
- Cloud-Based Solutions: These offer scalable infrastructure services including backup storage options ensuring business continuity even during disasters.
By implementing these technologies together, we create a layered defense system protecting us from various types of attacks while also reducing risk exposure.
Remember though, no single solution will guarantee 100% safety, so always stay vigilant!
Technology can help prevent cybercrime through multi-factor authentication (MFA) and other advanced security tools.
By combining something you know with something you have, MFA adds an extra layer of security making it much harder for hackers to gain unauthorized access.
Implementing these technologies together creates a layered defense system protecting us from various types of attacks while also reducing risk exposure.
State Laws On Cybercrimes, Prosecution And Penalties For Offenders
:max_bytes(150000):strip_icc()/Amazon_phishing_email_example-fb607939da584552882c501ec9ac913d.png)
Understanding Cybercrime Laws: Why It Matters
As an expert in cybercrime, I know that understanding the legal repercussions for offenders is essential.
With technology advancing at an unprecedented rate, our laws must evolve to keep up with emerging threats such as ID theft and computer fraud.
State Laws Regarding Cybercrimes
In addition to updating outdated statutes, some states have enacted specific laws aimed solely at addressing cybercrime problems within their borders.
It's important to understand state laws regarding Cybercrimes:
- Each U.S State can define its own set of crimes related to hacking into a computer system or stealing data
- Penalties for violators vary by jurisdiction from fines up tens of thousands dollars or more
- Law enforcement agencies now take online crime seriously but require efficient rules laid out by governments
- Some states offer resources like hotlines and websites where victims can report incidents and receive help
It's crucial that individuals stay informed about changes in legislation surrounding cybersecurity so they don't inadvertently break any laws while using technology.By staying aware of current regulations, we can work together towards preventing future instances of cybercrime.
What To Do If You’ve Been Phished: Reporting Incidents And Taking Action
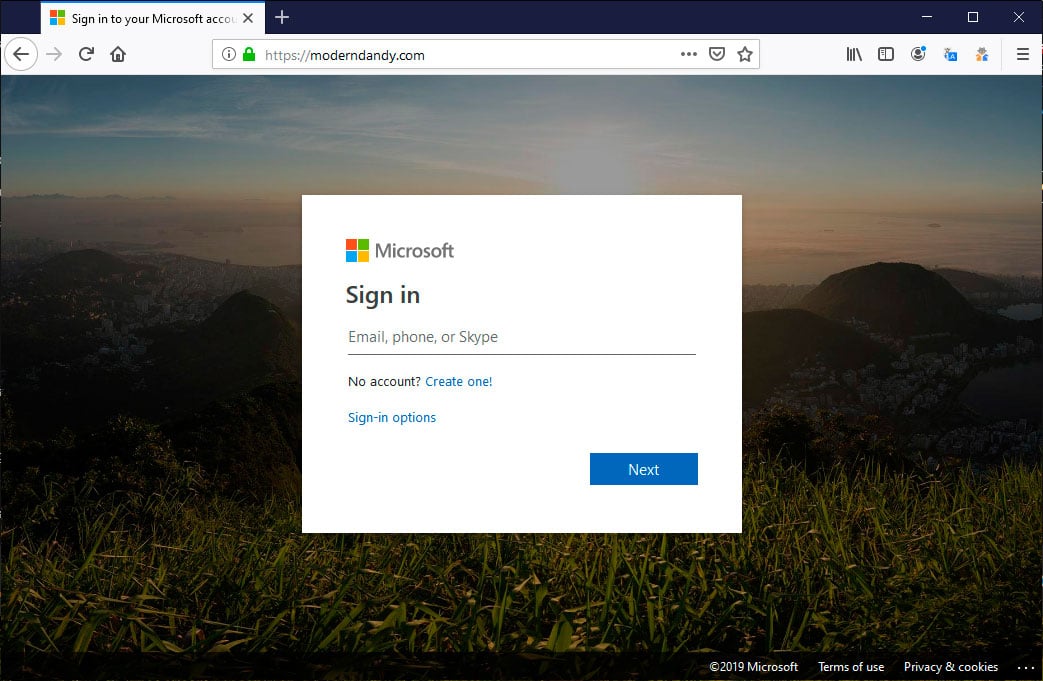
Protect Yourself from Phishing Attacks
As a cybersecurity expert, I know that anyone can fall victim to phishing attacks.
If you suspect that you have been phished, it's important not to panic and take immediate action by reporting the incident.
What to Do If You Suspect a Phishing Attack
The first step is crucial: contact your bank or credit card company right away if you suspect a phishing attack.
They will freeze accounts or prevent unauthorized access.
Next, change all login credentials for websites and apps where potential breaches may have occurred.
Use strong passwords with uppercase and lowercase letters, numbers, and symbols to make it difficult for hackers to gain access.
Protect Yourself from Cyber Threats
To further protect yourself from cyber threats:
- Check credit reports frequently
- Backup important data regularly
- Avoid public Wi-Fi networks as much as possible.
- Do not open emails from unknown sources
- Be wary of clicking on links in messages
Remember these tips are essential after experiencing a phishing attack; however, cybersecurity threats continue evolving rapidly so stay vigilant!
Training Employees On How To Avoid Dangerous Internet Mistakes That Open Their Devices And Systems Up To Hackers
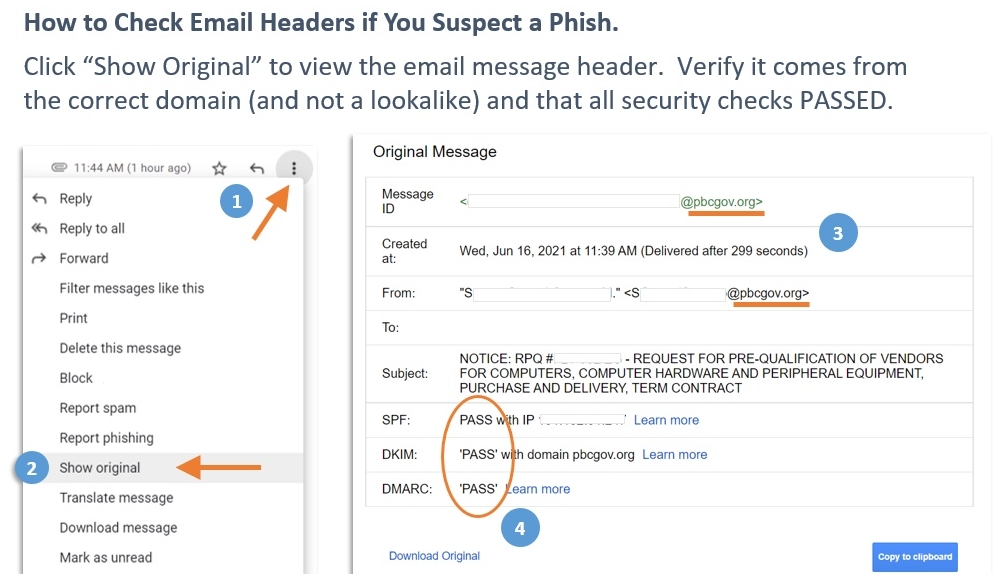
Why Employee Training is Crucial for Cybersecurity
As a cybersecurity expert, I believe that training employees is one of the most effective ways to protect a company from cybercrime.
Cybercriminals are becoming increasingly sophisticated, and even minor mistakes can lead to devastating consequences for businesses.
The Importance of Regular Cybersecurity Training
It's crucial for companies to provide regular cybersecurity training sessions for all employees.
These should cover basic security protocols like creating strong passwords and being cautious when opening emails or clicking links.
Additionally, more advanced topics such as identifying phishing attempts and recognizing social engineering tactics used by attackers must be explored comprehensively so that potential threats can be identified before they become problematic.
5 Important Points to Keep in Mind When Designing Your Cybersecurity Training Programs
- Engage learners: Training materials needn't be boring!
Keep them engaged through real-world examples of attacks.
- Make it relevant: Ensure that the content is tailored specifically towards your organization's needs.
- Reinforce learning: Provide opportunities for hands-on practice exercises after each session.
- Encourage reporting incidents: Create a culture where employees feel comfortable reporting any suspicious activity without fear of retribution.
- Stay up-to-date on emerging threats: Continuously update your program based on new trends and evolving risks.
By following these guidelines while developing employee education initiatives around cybersecurity awareness, you will create a safer environment within which business operations may thrive securely over time.
The Future Of Cybersecurity In The Digital Age
The Future of Cybersecurity
In my expert opinion, the future of cybersecurity will be marked by even more advanced and complex measures.
As technology evolves at a rapid pace, cybercriminals are always seeking new ways to exploit vulnerabilities in digital systems.
To avoid being targeted by hackers, it's crucial for both companies and individuals to stay up-to-date with the latest security protocols.
AI Integration
One major trend that I predict is an increase in artificial intelligence (AI) integration into cybersecurity systems.
AI can help identify potential threats before they cause any damage while analyzing large amounts of data much quicker than humans ever could.
This means faster response times and better protection against attacks.
Blockchain Technology
Another promising development is blockchain technology which may play a significant role in improving cybersecurity through decentralized databases that cannot be easily hacked or corrupted.
By creating secure networks where information is stored across multiple nodes rather than on one central server, we can reduce the risk of breaches significantly.
As our reliance on digital technologies continues to grow exponentially so does our need for robust security measures capable of keeping us safe from malicious actors online - whether those come from state-sponsored groups or individual criminals looking for easy targets like small businesses without adequate defenses set-up yet!
It's important to stay informed and take proactive steps to protect ourselves and our businesses from cyber threats.
By implementing the latest security measures and staying up-to-date with emerging technologies, we can stay one step ahead of cybercriminals and keep our digital systems safe and secure.
Final Takeaways
It was a typical day at work when I received an email from my bank. The subject line read "Urgent: Security Alert". My heart started racing as I opened the email. It looked legitimate, with the bank's logo and branding. The email stated that there had been suspicious activity on my account and that I needed to click on a link to verify my information. Without thinking twice, I clicked on the link and entered my login credentials. It wasn't until a few minutes later that I realized what had just happened. I had fallen victim to a phishing scam. Phishing is a type of cyber attack where scammers use fraudulent emails, text messages, or websites to trick people into giving away sensitive information such as passwords, credit card numbers, or social security numbers. These scammers often use social engineering tactics to create a sense of urgency or fear in their victims, making them more likely to fall for the scam. As the founder of AtOnce, an AI writing and customer service tool, I understand the importance of protecting sensitive information. That's why we use AI to help businesses create authentic and personalized customer interactions while also detecting and preventing phishing attempts. Our AI-powered chatbots can recognize and flag suspicious messages, alerting businesses to potential phishing attempts before they become a problem. By using AtOnce, businesses can provide their customers with a secure and trustworthy experience, while also protecting their own data. Don't be like me and fall for a phishing scam. Protect yourself and your business with AtOnce.Tired of struggling to come up with great content?
- Do you spend hours staring at a blank screen?
- Are you tired of mediocre writing that fails to convert?
- Does the thought of writing make you feel overwhelmed?
AtOnce's AI writing tool revolutionizes the writing process, making it fast, easy, and effective.
- Generate high-quality content in minutes, not hours.
- Write clear and concise copy that engages your audience.
- Increase conversions with powerful marketing messages.
- Save time and increase productivity with automated writing.
AtOnce's AI writing tool uses advanced algorithms to analyze your writing style and generate content that sounds like you.
- Choose from a wide range of writing styles to match your brand voice.
- Create engaging blog posts, product descriptions, emails, and more.
- Get instant suggestions for improving your writing and increasing conversions.
- Monitor your results and track your success with real-time analytics.
With AtOnce's AI writing tool, you can:
- Save time and increase productivity
- Improve your writing skills and develop your unique voice
- Create high-quality content that engages your audience and drives conversions
- Track your results and measure your success
Start revolutionizing your writing today
Don't let the stress of writing hold you back.
With AtOnce's AI writing tool, you can create high-quality content that engages your audience and drives conversions. Sign up today and start revolutionizing your writing!What is phishing?
Phishing is a type of cyber attack where attackers send fraudulent emails or messages to trick individuals into providing sensitive information such as login credentials, credit card numbers, or personal information.
How can I protect myself from phishing?
To protect yourself from phishing, you should always verify the sender's email address, avoid clicking on suspicious links or downloading attachments from unknown sources, and enable two-factor authentication for your accounts.
What should I do if I fall victim to a phishing attack?
If you fall victim to a phishing attack, you should immediately change your passwords for all affected accounts, contact your bank or credit card company to report any fraudulent charges, and consider freezing your credit to prevent identity theft.
